"Hey—I have this crazy idea. What if the POSTs django-inplaceedit
processes are totally exploitable?"
Security Hilarity
And so our journey down the rabbit hole began. It turns out that you should probably never include little-used open source software that modifies entries in your database while making the assumption that it's secure.
I believe the following code speaks for itself:
def test_will_inplaceedit_allow_us_to_pwn_ourselves(self):
# Asheesh: "total cost of pwnership: 1 test"
# note: user paulproteus has poor password hygiene
u = User.objects.create(username='paulproteus', password='password')
u.save()
self.client.post(
'/inplaceeditform/save/',
{
"app_label": "auth", # the django app
"module_name": "user", # the django table
"field_name": "username", # the field name
"obj_id": u.pk, # the pk
"value": '"LOLPWNED"' # new value
})
self.assertEqual(User.objects.get(pk=u.pk).username, "LOLPWNED")
Carefully crafting this payload involved very little effort; watching this test pass was a little bit horrifying.
The problem stems from the way django-inplaceedit sets up user permissions;
their docs give an example of only allowing superusers edit access, which would
suggest an internal or authenticated use case. But we want our bugsets to be
publicly editable... and given that this is the way we set up our permissions,
we also implicitly gave the entire public internet the ability to edit our
entire database. Wow.
Lesson learned: trust no one. Or, at least restrict access to the bugsets app
tables. For now, we've disabled this by turning off edit access in production.
We also plan to make an upstream pull request to the django-inplaceedit docs
to help others avoid this kind of security issue in the future. We also created
(and addressed) an
issue to track this fun adventure.
Development
Development for this period started off a little delayed due to lack of Asheesh
availability, and development on the main project was delayed slightly by the
GIANT SECURITY HOLE django-inplaceedit introduced, but we sure wrote a lot of
code in the end.
gsoc14.10 and gsoc14.11 deliverables
These two weeks saw the end of the long-standing issue995:
- Fix
django-inplaceeditCSS to make the screen usable - YAGNI simplification of
AnnotatedBugfields
This milestone was pushed back again due to difficulty with CSS and issues that continually arose every time existing ones were fixed. Here's a code sample that reflects the majority of these two weeks' development.
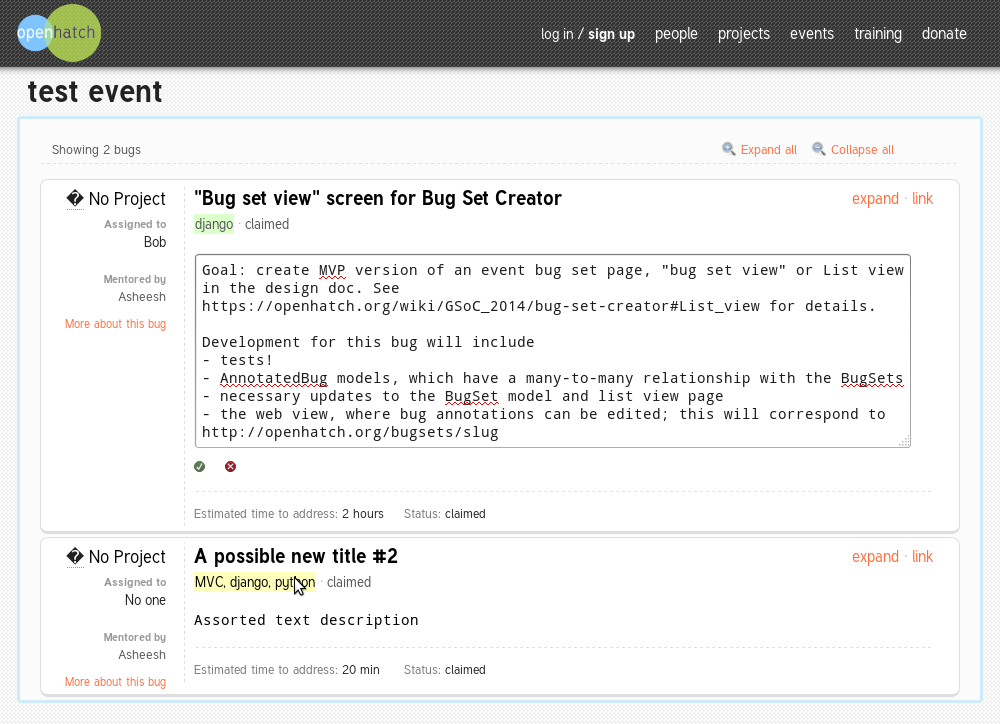
Figure 1: CSS successfully coerced into exhibiting beauty
gsoc14.12 deliverables
This milestone saw major development of the create/edit view (tracking issue).
Asheesh and I fought with Django forms, many tests, and mostly emerged victorious.
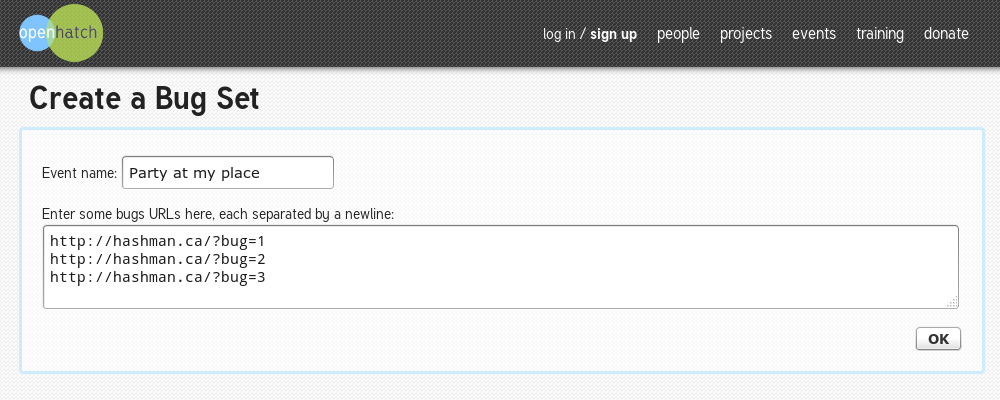
Figure 2: Create a bug set
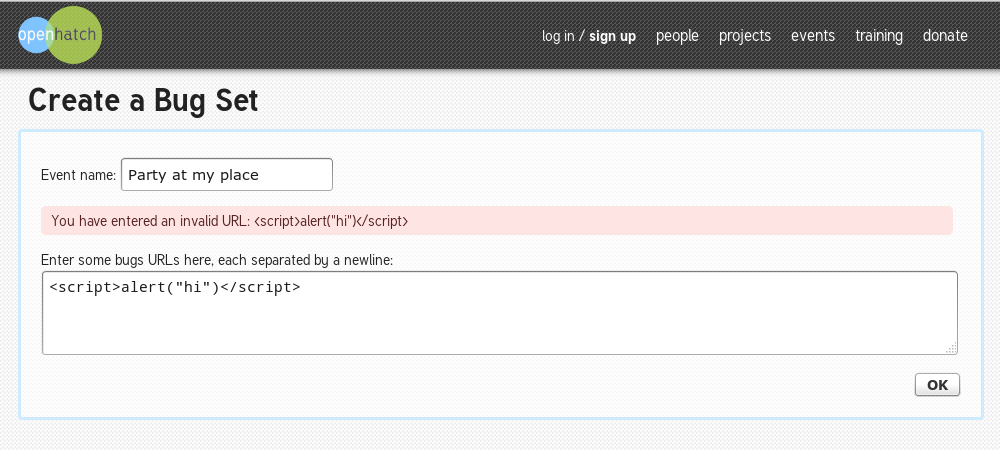
Figure 3: You can't inject javascript!
What's next
There are a number of features we've discussed implementing for the last few weeks. But here's what we have planned:
- Finishing up the edit view
- Update list view to include edit links (while logged in)
- Simultaneous editing: async notification if loaded page values have changed
- Security fixes to re-enable editing in production
- Refresh button for associated metadata we have in the OpenHatch bug db
- User testing
- Documentation
Obstacles
There have been two main issues the past few weeks: CSS issues and availability. As I've lamented about CSS in my last post, I'll discuss the availability problem in a bit more detail.
Since returning from OSBridge, Asheesh and I have been a bit busy playing catchup with school and work. In particular, since Asheesh' availability has been even less than that of the dreaded "working adult with a life outside of job," we've had a lot less time to sync up and pair. And due to catching up on assignments and course wrapup, I was able to complete less GSoC work than I might have if Asheesh was babysitting me in some pairing sessions.
In regard to the CSS, in the end I managed to figure it out! A big thanks to Rachelle Saunders, who I met at a local Women Who Code meetup, and was able to solve all my woes in all of 5 fateful minutes. You rock, lady! (A moment of silence for all those hours I could have spent fighting with this on my own. Tears shed for the loss of this valuable learning experience.)
Comments
You are invited to send your comments or feedback to the project mailing list!